Repair JPEG Images Affected by STOP/DJVU Ransomware
Manisha Rawat
|
Updated On - October 09, 2023
Read time 7 minutes
Are you a victim of STOP/DJVU ransomware, and have been not able to access files on your machine? Are you indecisive about what to do next? Well, the first step would be not to pay the attacker. What next? Let us take you through it. You will need a little in-depth understanding as there is no simple solution to this kind of problem. Further, you need to be better prepared to avoid such attacks in the future.
Ransomware is a type of malware that blocks a user’s access to the data or threatens to make it public unless the user/victim agrees to pay a ransom. Ransomware is based on using cryptography to develop malicious software. Often, attackers use a trojan disguised as a legitimate file that spreads quickly into the system and encrypts the files. These files are locked by the malware and can only be accessed by decryption using the cryptographic key. Usually, the malware creates a message file on the system, informing the victim of the attack and how to pay the ransom in exchange for a decryption key.
DJVU ransomware belongs to the STOP family of ransomware. It was first observed around December 2018 and has been very actively attacking users all around the world. It is mostly packaged in software crack packages, keygens, or adware bundles available on torrent sites or other platforms. Once the infected file is run, the trojan quickly spreads encryption malware in the background infecting the system at a very fast pace. Main file types targeted are .doc, .pdf, .jpg, .jpeg, .mp4 and other popular file/application formats. The ransomware doesn’t encrypt the file completely, but only around 5 MB of it. Once the malware encrypts the files, files are updated with .djvu extension or other similar extensions. Further, _openme.txt or _readme.txt files appear on the desktop. These files are basically ransom notes and contain details about the mode of payment and other such details.
Example of Ransom Note:
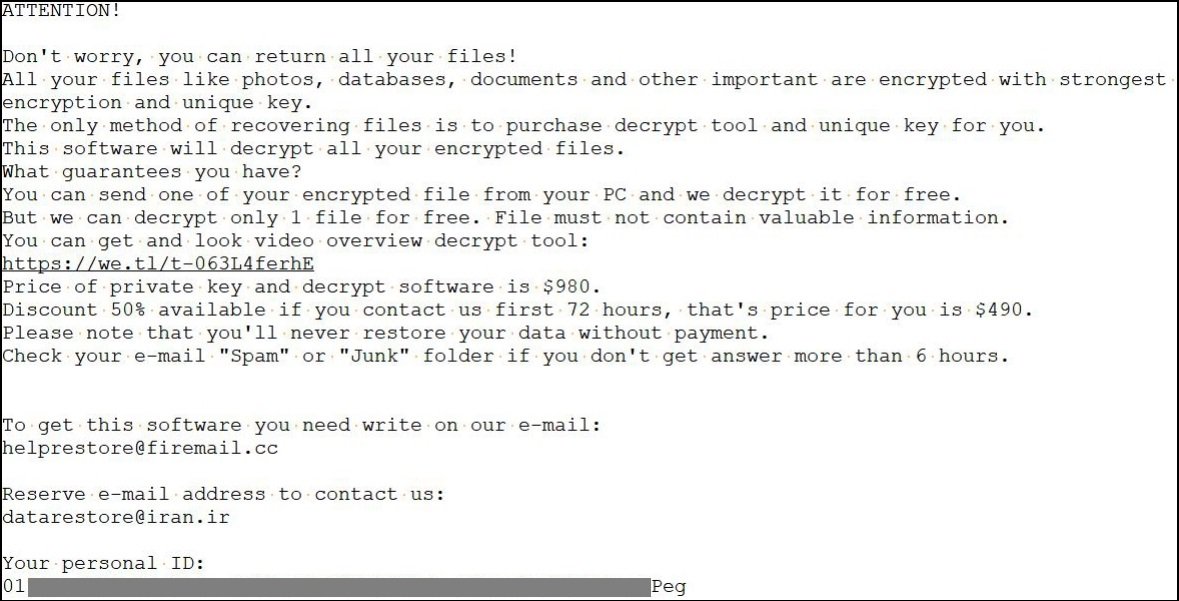
The virus also deletes disk backups, updates Windows registry entries, and updates various other system files, which makes it almost impossible to restore or recover the impacted data and files.
Let us just explain a little about the ransomware before we move further. DJVU cryptoware encrypts your files using a single key. If your PC is connected to the Internet, it may use the key online. However, if, for some reason, the system is not able to connect to their server, it uses an encryption key bundled in malware code. If this is the case, the decryption of files is possible without paying a ransom.
Now, we have explained all that you need to know to proceed further. You are aware of how the attack has worked so far. It will be easy to understand each of the steps we suggest from here on.
Below is the step-by-step manual on how to use this tool:

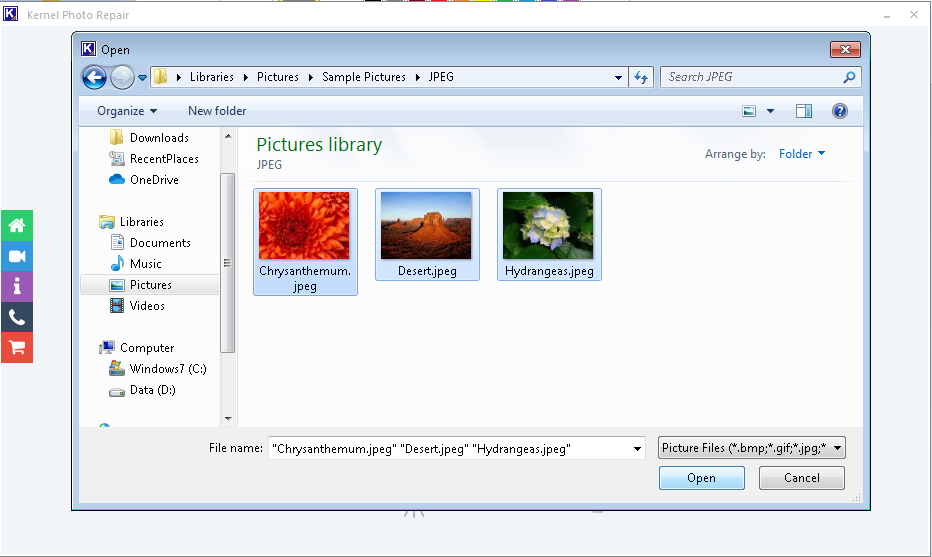
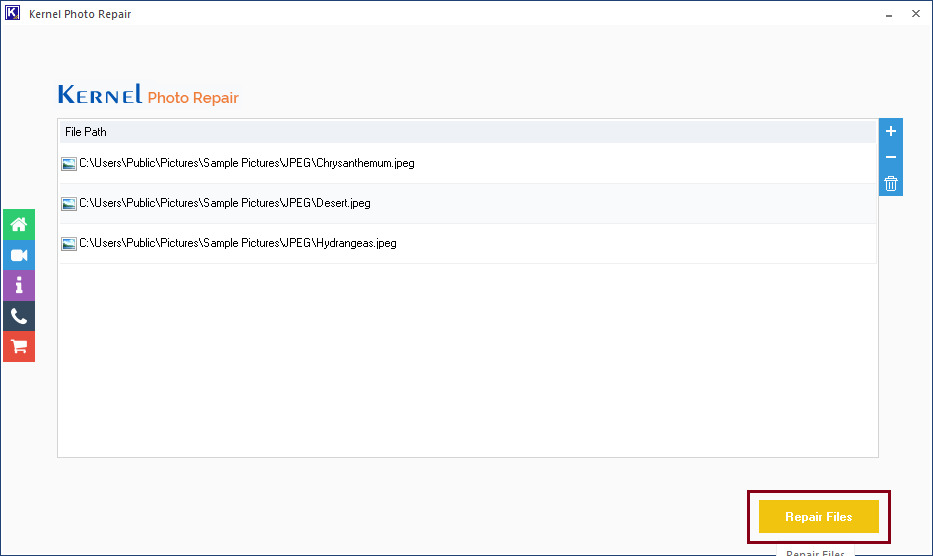
Note: You can click on the (+) sign on the top right to add more files or (-) sign to remove unwanted files.
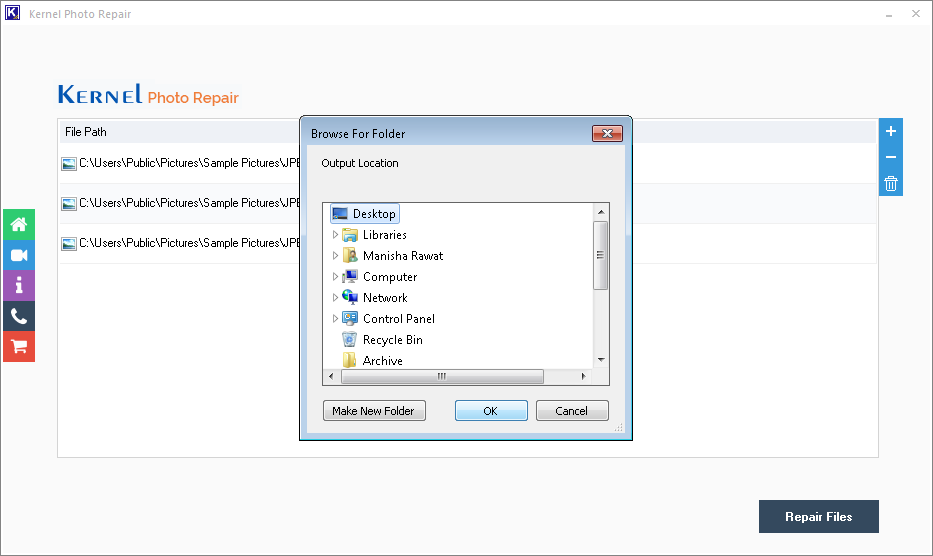
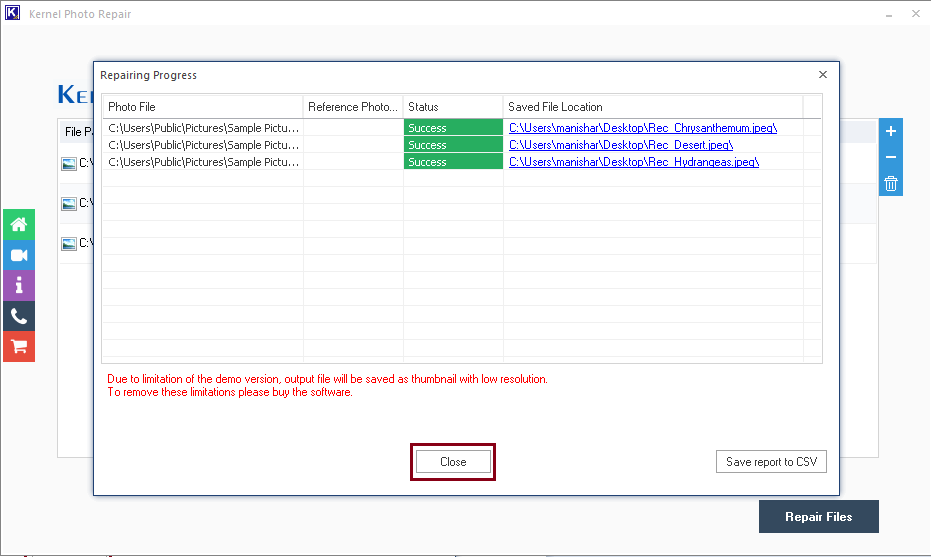
Note: You can choose to save the report by clicking on the ‘Save report to CSV’ button.
Now, your photos should be repaired. You can now access them in the output folder path provided during the steps mentioned above.
In this blog, we discussed what is ransomware and how these attack on victim systems. Then, we explained the DJVU ransomware and how it works. We explained the ransom notes, what kind of files are targeted by the ransomware and how the encryption of your files is done. We briefly covered the use of trojan and partial encryption of files to attack more and more files in very less time. Offline and online encryption methods were covered, and the solutions for each of the methods were explained. Lastly, we covered how to utilize this software to repair encrypted JPEG files. This tool can repair inaccessible JPEG files in no time and can be used to fix multiple files in one go. We hope this blog helped you.
Thanks for sharing this article, I download this software and used it. It was very useful.